Hi all,
Wanted to share some news on Microsoft Authenticator new features for this Friday.
Table of Contents
Generating Strong passwords
Cool feature, that wasn’t there before. Yep, it wasn’t. See the screenshots for more insights.
Enable Autofill with Authenticator
How do I turn on password autofill in Authenticator on my phone?
- Open the Authenticator app.
- On the Passwords tab in Authenticator, select Sign in with Microsoft and sign in using your Microsoft account. This feature currently supports only Microsoft accounts and doesn’t yet support work or school accounts.
How do I make Authenticator the default autofill provider on my phone?
- Open the Authenticator app.
- On the Passwords tab inside the app, select Sign in with Microsoft and sign in using your Microsoft account.
- Do one of the following:
- On iOS, under Settings, select How to turn on Autofill in the Autofill settings section to learn how to set Authenticator as the default autofill provider.
- On Android, under Settings, select Set as Autofill provider in the Autofill settings section.
Note! Autofill is not currently available for work or school accounts.
And also an Extension to use in Chromium based browsers.

GPS locations
You can choose GPS location in Named locations.


And when you enforce it, user will be sent a consent for sharing their location.

And you will be asked to share your location with authenticator (Sorry for the screenshots are in Finnish but you get the point)

A Conditional Access policy with GPS-based named locations in report-only mode prompts users to share their GPS location, even though they aren’t blocked from signing in.
GPS location doesn’t work with passwordless authentication methods.
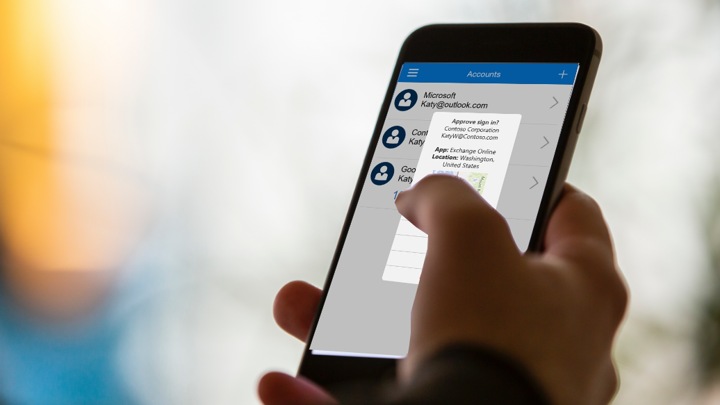
Number matching (Preview)
Microsoft has released number matching (yes, the same feature than is used for MS Account and passwordless sign-in)
Number matching is a key security upgrade to traditional second factor notifications in the Microsoft Authenticator app that will be enabled by default for all tenants a few months after general availability (GA).
We highly recommend enabling number matching in the near-term for improved sign-in security.
It will be available for the following scenarios.
- Multifactor authentication
- Self-service password reset
- Combined SSPR and MFA registration during Authenticator app set up
- AD FS adapter
- NPS extension
And this is how you enable it.
Go to authentication methods and choose a group. As of now it has to be either one, cannot choose “All users” or particular user.

Then under the three dots, choose enabled.

And once enabled, you will receive the number on the screen that you have to write to Microsoft Authenticator app.

Known issues
- Number matching for admin roles during SSPR is pending and unavailable for a couple days.
Limitations and notes with these features
If users or groups are a member of over 2048 groups their access may be blocked. This limit applies to both direct and nested group membership.
Number matching can only be enabled for a single group.
For passwordless users, enabling number matching has no impact because it’s already part of the passwordless experience.
Number matching for admin roles during SSPR is pending and unavailable for a couple days.
Number matching is a key security upgrade to traditional second factor notifications in the Microsoft Authenticator app that will be enabled by default for all tenants a few months after general availability (GA).
End conclusions
Number matching is a really nice addition to make your experience more secure. Also the GPS location sharing is excellent, now you can now the location where the sign-in that you are approving is coming.
With Microsoft Managed Settings, admins can trust Microsoft to enable a security feature they have not explicitly disabled.
This is proactive security in practice!
Stay tuned for more!







 RSS - Posts
RSS - Posts