
This is the first part of Identity blog series.
“Identity is the new perimeter” was probably first said in 2018 at Identiverse. And it is actually true, identity is all you have in the Evergreen cloud service.
There can’t be traditional firewalls in front of identity as it cannot be protected this way. Of course there are still old school firewall in front of company perimeters, employee laptops. Companies and individuals protect their wireless networks, use vpn-connections to protect the data that goes in and out the their networks. That’s also important.
But how do you protect something that doesn’t have a port, It doesn’t follow patterns like network traffic does or does it?
As always I’m looking the world thru Microsoft shaped glasses, they do an amazing job with securing identity and data that travels in the network. Insane amount of identity request flow thru their systems and MSRC is all the time evolving the protection landscape with diagnostics help of these massive flow of information.
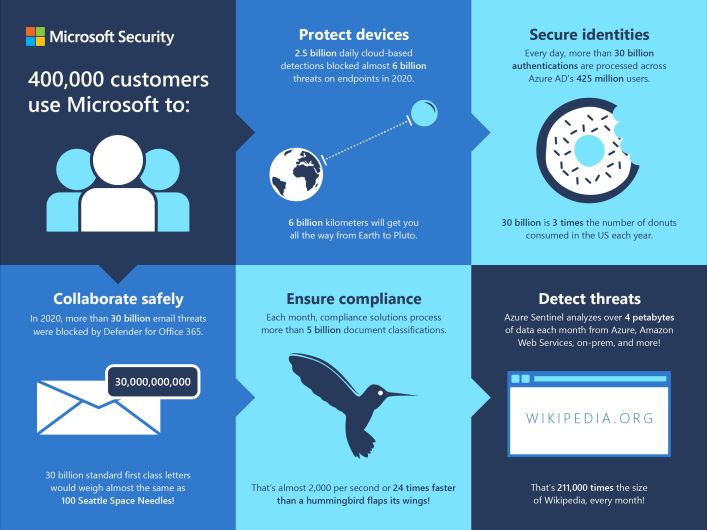

So like I said I look the world thru Microsoft glasses and seeing those numbers make it a good choice. Of course the other Cloud service providers like Amazon have big share of world-wide pandemic accelerated consumption also.
It really depends on the assets that you compare from the wide collections of these giants. It’s like any other business, other one is bigger at times than the other.
When discovering content for this post I stumbled upon this article.

And it was stating that in UK CIO choose Microsoft because they have provide the identity and access management cross environments.
“The Microsoft vs Google vs AWS question has a straightforward answer: while all three cover the basics of identity management, and have their own strengths, the choice will really come down to your environment: whether it is mostly on-prem, cloud or hybrid, and which company is your major cloud provider.
Although growing, boosted by the growth of remote work in 2020, cloud has had a slower adoption in identity and access management than other business areas, with only 28 per cent of our respondents running a full cloud solution. A product that can operate across environments is generally preferred.
Many CIOs adopt both Active Directory and Azure Active Directory for this very reason, but that is difficult with the cloud-first tools from Google and AWS.”
And that’s true, they do and let’s see how they do it from the identity perspective, first from the cloud point of view.
Azure AD Identity protection
AAD Identity protection is has a lot to offer, it’s an comprehensive suite of world-class security tools.
Security Overview

The Security overview is broadly divided into two sections:
- Trends, on the left, provide a timeline of risk in your organization.
- Tiles, on the right, highlight the key ongoing issues in your organization and suggest how to quickly take action.
Identity Secure Score
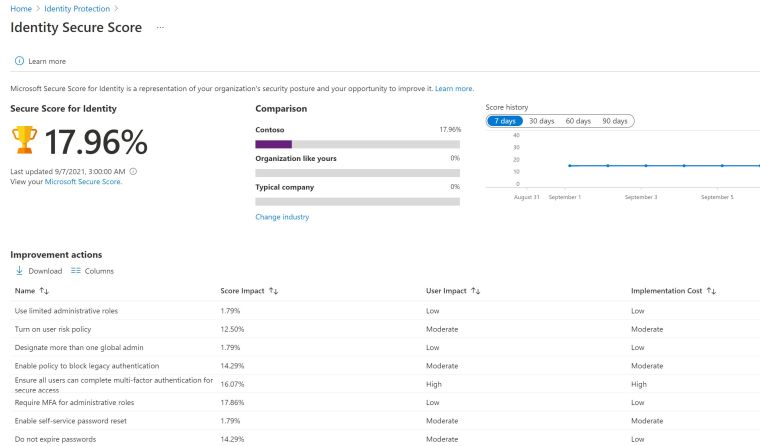
The Identity Secure Score measures and compares your security posture to industry patterns. You can choose your industry in get comparison against the average in your segment.

And back to Identity protection.
What is a user risk?
Identifies and responds to user accounts that may have compromised credentials. Can prompt the user to create a new password.
What is a sign-in risk?
Identifies and responds to suspicious sign-in attempts. Can prompt the user to provide additional forms of verification using Azure AD Multi-Factor Authentication.
And what can you do with MFA registration policy?
Makes sure users are registered for Azure AD Multi-Factor Authentication. If a sign-in risk policy prompts for MFA, the user must already be registered for Azure AD Multi-Factor Authentication.
And what controls there are?

When you enable a policy user or sign in risk policy, you can also choose the threshold for risk level – low and above, medium and above, or high. This flexibility lets you decide how aggressive you want to be in enforcing any controls for suspicious sign-in events.
And what about the reporting features?

With reports you can see the risky user, logins and what was detected and if you click the Detection time you can see more detail.

And if you click Additional info, it will open Cloud App Security to investigate even further. You can view

And you cloud create policies based in the info you discover and prevent other malicious logons.

So as you can see there is really good controls for securing user identity and making sure that your identity is safe. If you want receive emails for user when risk events happen and / or weekly basis it’s also possible.



This is just the basis of Identity protection in Azure and there is much more to come in coming blogs.
Stay tuned for part two of this series.
Over and out!




 RSS - Posts
RSS - Posts