
Then we go to Defender for Cloud and starting with the planning part. Let’s get going! Be sure to check the previous chapters, you will need that information to understand to journey that we are on.
Table of Contents
Plan and configure Microsoft Defender for Cloud settings, including selecting target subscriptions and workspaces
You should plan your environment accordingly for an holistic and truthful view of the landscape. When you have all the bits and pieces in place it makes everyday easier.
Subscriptions and Management groups
Be familiar with your organization’s structure and hierarchy, including your management group and subscription structure. This way you can design to what scopes you have to apply your protection and alerts.

Resources and policies
Recognize your compliance and regulatory requirements and align your security controls to meet them. This the next step on designing how to implement security to your environment, you have to know what resources there are to design how to secure and monitor them.
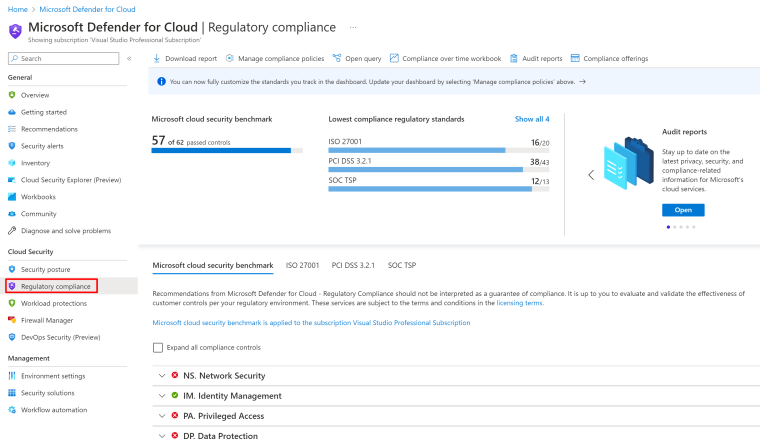
See the different compliance controls. Microsoft Defender for Cloud applies security initiatives to your subscriptions, a set of initiatives has many security policies under them.

The following options are provided by Defender for Cloud for collaborating with security policies and initiatives:
- See and alter the pre-installed default initiative – All Defender for Cloud registered subscribers are automatically allocated the “Microsoft cloud security benchmark” initiative once Defender for Cloud is enabled. You can update a policy’s settings to allow or disable certain policies inside the initiative. To learn about the alternatives accessible right out of the box, consult the list of built-in security policies.
- Add your own unique initiatives – Under Defender for Cloud, you may alter the security measures used in accordance with your subscription. If your machines fail to adhere to the policies you establish, you will then get suggestions. See Utilizing custom security initiatives and policies for details on how to create and assign custom policies.
- Add regulatory compliance standards as initiatives. Defender for Cloud’s regulatory compliance dashboard displays the current status of all evaluations made in your environment in relation to a certain standard or legislation to enhance your regulatory compliance for additional details.
Determine the types of workloads and assets that must be protected in the cloud.

Continuous export
The security alerts and suggestions generated by Microsoft Defender for Cloud are in-depth. You may export these warnings and suggestions to Azure Log Analytics, Event Hubs, or another SIEM, SOAR, or IT Service Management system to examine the data contained within. The warnings and suggestions can be streamed as they are created, or you can set a timetable to transmit periodic snapshots of all the fresh data.
You have complete control over what will be exported and where with continuous export. You may set it up such, for instance:
- To an Azure event hub, all high severity warnings are delivered.
- Your SQL servers’ vulnerability assessment scan results are forwarded to a dedicated Log Analytics workspace for all discoveries with a medium or higher severity.
- Every time suggestions are created, they are sent to an event hub or a workspace for Log Analytics.
- Every time the score for a control changes by more than 0.01, the secure score for a subscription is delivered to a Log Analytics workspace.
| Required roles and permissions: | Security admin or Owner on the resource groupWrite permissions for the target resource.If you’re using the Azure Policy ‘DeployIfNotExist’ policies, you’ll also need permissions for assigning policiesTo export data to Event Hubs, you’ll need Write permission on the Event Hubs Policy.To export to a Log Analytics workspace:if it has the SecurityCenterFree solution, you’ll need a minimum of read permissions for the workspace solution: Microsoft.OperationsManagement/solutions/readif it doesn’t have the SecurityCenterFree solution, you’ll need write permissions for the workspace solution: Microsoft.OperationsManagement/solutions/actionLearn more about Azure Monitor and Log Analytics workspace solutions |
You will find the options under Environment settings

And you can also export to Third-party SIEM solutions

Alerts and triggers
And finally determine the type of alerts you want to receive, the frequency with which you want to receive them, and the severity levels.
In example you send email notifications

See more from Learn

Support matrix gives you an good overview of the different features inside the suite, what solutions can be used for what

But did you know that you can also demo them yourself without them real life alerts. You can generate own own alerts with sample alerts.
Create sample alerts (Preview)

You can even choose which Defender plans you want to use, so cool and for future note, Sentinel has also these samples available but later on that.
Just choose the plans and hit “Create samples alerts” and see the magic happen.


And done, this is so cool and really help you do educate yourself with out doing any harm for production environments.

So now we some alerts, let’s see what we can do. When you open that alert, you can see Take action or View full details.

Then you can create an Logic app to prevent future harm for similar alerts or to Configure those email settings I showed before.

Here the GitHub repo that hosts Workflow automation templates that you can use and if you want to be super-helpful, you can also contribute there yourself. It will help to to understand what needs to be done inside those Playbooks (which we will cover later in this series)
Configure Microsoft Defender for Cloud roles
Azure role-based access control (Azure RBAC), which offers pre-built roles that can be applied to users, groups, and services in Azure, is used by Microsoft Defender for Cloud.
Defender for Cloud analyzes your resources’ settings to find security flaws and vulnerabilities. When you have been given the Owner, Contributor, or Reader role for the subscription or resource group that a resource belongs to in Defender for Cloud, you can only see information about that resource.
The following roles and be defined for Defender for Cloud
| Action | Security Reader / Reader | Security Admin | Contributor / Owner | Contributor | Owner |
|---|---|---|---|---|---|
| (Resource group level) | (Subscription level) | (Subscription level) | |||
| Add/assign initiatives (including) regulatory compliance standards) | – | ✔ | – | – | ✔ |
| Edit security policy | – | ✔ | – | – | ✔ |
| Enable / disable Microsoft Defender plans | – | ✔ | – | ✔ | ✔ |
| Dismiss alerts | – | ✔ | – | ✔ | ✔ |
| Apply security recommendations for a resource (and use Fix) | – | – | ✔ | ✔ | ✔ |
| View alerts and recommendations | ✔ | ✔ | ✔ | ✔ | ✔ |
You must be a Security Admin, Owner, or Contributor of that subscription in order to change a security policy.
In the beginning I noted that you should understand the structure of your tenant, management groups and relation to your subscriptions.
Well also with permission this is accurate, you need to define them on different levels, depending on the structures.
See more from Learn on RBAC policies and how they work.

Assess and recommend cloud workload protection
Defender for Cloud gives you multiple different plans that you can use to protect your workloads, let’s see what they are.
First navigate yourself to Environment settings.

And once you click you subscription, you will those plans seperately.

If you choose Settings & monitoring in the top, you will see the following for all the workloads

So it really depends on what you have inside your environment, once you enable a plan, it will be protected and you can create custom rules depending on the different aspects that you see fit.
See more from Learn

Identify and remediate security risks using the Microsoft Defender for Cloud Secure Score
Advanced security analytics are used by Defender for Cloud, which go well beyond signature-based defenses. Using advances in big data and machine learning technology, events across the whole cloud fabric are evaluated in order to discover threats that would be hard to spot using human methods and anticipate the trajectory of assaults.

Microsoft will collect the information by analyzing multiple sources of data.

See more from Learn

Using portal
You can do it with the portal from Security posture page

See more from Learn

Using API
For most organization it would be wise to APIs to access the content, they will give more possibilities to automation than ClickOps based approach.

And here is a good sample on how to do it with an PowerShell script.
And then maybe doing the automation with Defender for Cloud APIs

Or if you prefer PowerShell based scripts, here you go
Manage policies for regulatory compliance
Again that multi-cloud could be here if you have those other cloud in use, you can get all the benefit from this.
But if you don’t, then only Azure, let’s how to make you environments compliant based on the regulations.

Click Governance rules to create your first rule

When you start creating a rule, it will ask you for the following information, it will also allow you to apply an grace period if needed.

And once created, you can apply it to all of your resources (which you already know, right?)

You are variety of compliance policies ready.

If you don’t wait to use all of the ASB 192 audit policies, just hit create an exemption.

Once you edit the initiative (which is a collection of policies) you will see the following.

you can even can add resource selectors and Overrides if needed.

In the parameter page you can edit different aspects of how the policies will interact with your assets.

And with what to remediate those assets if needed and required by the policy.

And define those non-compliant messages that will be displayed under the resources.

And you can disable those initiatives or even add your custom ones.

Here is the list of standard ready for use, if needed.

If you choose to create your own, you can still use templates for definitions as automated or Microsoft managed.

You can choose both of them and even edit the controls


Review and remediate security recommendations
Security recommendations have some overlapping with Defender Secure score, which is understandable as there a lot same components they look after for.

To dig a little bit deeper, you will the actions under the grouped items.

When using multi-cloud based holistic view, you will those other cloud in the same page. Which makes it easier to get a comprehensive view for your security landscape

Cloud security explorer (preview)
You can also use Cloud security explorer to discover those different assets and their statuses. It will open an query for you

And once you choose an asset, you can drill down deeper on what to search for.

And if you in example your storage accounts, you can find out those recommendations from here.

Upcoming changes
There is always changes in the evergreen solutions, Defender for Cloud isn’t an exception.
Closure
Understand how your hierarchy is built. Realize how Subscriptions and Management groups work and what resources are attached to what.
Also give notice for Tags that are in use, they will help you a lot to categorize the resources and policies.
How do alerts work and what you actions you can take on them?
What RBAC roles give what permissions and how you can define those roles.
What workloads you can protect and how to determinate the remediations with Secure score with Azure Portal or APIs
If renewing, keep track of upcoming changes!
You can also validate your alerts for different workload, see more from Learn.

Labs
Here some labs for you to get that study going
| Module | Lab |
|---|---|
| Learning Path 3 – Mitigate threats using Microsoft Defender for Cloud | Exercise 1 – Enable Microsoft Defender for Cloud |
| Learning Path 3 – Mitigate threats using Microsoft Defender for Cloud | Exercise 2 – Mitigate threats using Microsoft Defender for Cloud |
Link to main post


 RSS - Posts
RSS - Posts