
Table of Contents
Deploying external server to Defender for Cloud
Deploying those servers can be done with the following methods:
- Using Azure Arc-enabled servers (recommended)
- From Defender for Cloud’s pages in the Azure portal
And this is the reason we are talking about Arc as an onboarding tools.

See more here

But as many use Azure for your VMs and once you do, you will have some troubles on connecting to some services that are supposed to be used for outside Azure servers, one of them being Azure Arc.
The error?
Add your server to Azure Arc, define RSGs, operating system version and connection type

And generate the script based on these parameters

When you onboard your resource to Arc and download the script, you will get this warning statement, what a huge bummer.

Why this happens?
For a couple of reason and one of them being
VM extensions
Extensions are compact programs that offer automation and post-deployment setup for Azure virtual machines. (VMs). Numerous extensions for VM configuration, monitoring, security, and utility apps are available on the Azure platform. The installation process is made simpler by publishers who take a program and wrap it in an extension.
The agent for Azure Arc-enabled servers cannot handle VM extensions that have already been deployed to the VM, despite the fact that they support many of the same extensions as Azure VMs. So, you have to remove them.
169.254.169.254 or IMDS IP
This IP is commonly used with all Cloud providers and in Azure it will give the VM the following Metadata information: the SKU, storage, network configurations, and upcoming maintenance events and more
So it it will check your Azure VM licensing and activation, this is the reason the blocking is meant for Evaluation purposes only. The following is one thing, you will surely see when you boot the VM for the first time.

See more from Learn

For AWS https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/instancedata-data-retrieval.html
For Google https://cloud.google.com/compute/docs/metadata/querying-metadata
How to “fix” it?
Open you VM in Azure portal and choose Extensions from the left-hand pane. If the VM has any installed extensions, choose each one separately, then choose Uninstall.

Then run the following commands inside the VM.
|
1 2 3 4 5 6 7 8 |
# Set Azure guest agent to disable state Set-Service WindowsAzureGuestAgent -StartupType Disabled -Verbose # Stop the service Stop-Service WindowsAzureGuestAgent -Force -Verbose # Create a Windows Firewall rule to block access New-NetFirewallRule -Name BlockAzureIMDS -DisplayName "Block access to Azure IMDS" -Enabled True -Profile Any -Direction Outbound -Action Block -RemoteAddress 169.254.169.254 |
Stopping the service

And the firewall block

And happy times!

And the server will magically appear in the portal

Defender for Cloud view
It takes some time for the server to be seen inside Defender for Cloud inventory.

If you open the server, you will those recommendations (Azure policies) that you should be compliant with based on the resource type

Testing it out
Because it is not a virus and contains no pieces of viral code, it is safe to spread.
It is also brief and easy to construct using a standard text editor because it is solely made up of readable ASCII characters.
As long as the file begins with the first 68 of the following characters and is precisely 68 bytes long, any antivirus program that supports the EICAR test file should be able to identify it in any file:
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
Read more from Eicar here,
You can down an test malware file here https://secure.eicar.org/eicar.com.txt
Or with this
|
1 2 3 4 5 6 7 8 9 10 11 |
# Define output file and path $path = "c:\folder\eicar.txt" # Define URI for the source $uri = "https://secure.eicar.org/eicar.com.txt" # Get the file to the path Invoke-WebRequest -Uri $uri -OutFile $path |
Once you download (just download, don’t have to run anything) the file and disable Defender for Endpoint and Antivirus or exclude the location that the file will be downloaded to, you will see this inside Defender for Cloud
Under alerts under the server, you can see the different alerts

And the details for the alerts and event Threat Information for Eicar

And it will be clearly saying that it’s not a real threat https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?name=Virus:DOS/EICAR_Test_File which is kind of funny.

Closure
How cool is that, testing things out in the comfort of your own Azure tenant. Don’t have to go far from home to achieve this.
There is also other good news for the masses, masses meaning many SQL in this sentence. You can also onboard all your SQL-servers at scale with Azure Policy
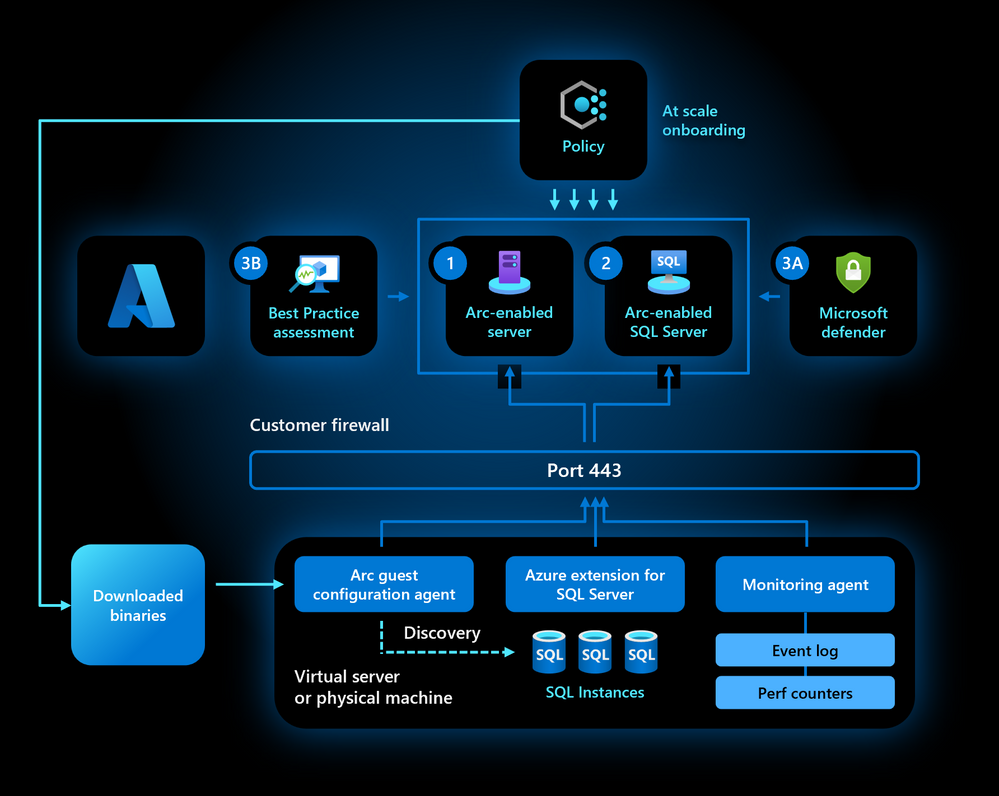
Happy times and happy Easter to all!


 RSS - Posts
RSS - Posts