Hi again,
Now to my all-time favorite topic, Exchange covered with identity and security.

How many times have see the error above when running HCW as an Exchange admin, I bet many and we will get to this later on.
Exchange has many use scenarios in the Microsoft Evergreen Services model. It can be used with Microsoft 365 groups, sharing calendars outside the organization or just sending emails.
In Microsoft 365 Exchange identity is named by your cloud username, the username can flow from on-premises AD if you have a hybrid configuration in-place and there fore local AD is your source of authority.
Or you can create your identity only as cloud-based. It doesn’t really matter.
If your identity is created only to the cloud, the on-premises doesn’t know it exists because it isn’t in the Global Address List on the other side, for this info to flow you need mail-user on the other side to define the address where the mail is routed (see info TargetAddress)
This is because on-premises and Exchange Online are different organizations that rely on federation and connectors for the rights and mail flow.

There two different major ways to the Hybrid to work, Classic and Modern. There is a lot of differences with these, but I will explain at the high level.
Classic is based on connectors, sharing rights on the mailboxes (specially in the Shared Mailboxes) and calendars. Everything have to be on both environments for them to work.
Classic also exposes Exchange Web Services and transport to the Internet.
Classic hybrid debugging is a mess if the config wasn’t done correctly and the Cumulative Updates aren’t at n-1 level (One version under current version)
With Modern Hybrid solution you can make it a bit easier. You install a agent service anywhere in our organization and will use MSFT provided proxy services to expose Exchange to the internet, so it’s much safer and easier. You don’t need to publish EWS to the internet and that will be one more attack surface less. Like you probably know, there has been a lot of vulnerabilities inside Exchange services in the past year (See info from MST https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34523), but still nearly not all the servers have been updated.

With Modern Agent Hybrid you can also directly migrate mailboxes thru MSFT Proxy’s, it’s a little bit slower, but works like a charm.
So with Modern hybrid there are many points why to use it.
According to MSFT best practices the mail flow should be coming thru Exchange Online Proctect (EOP)

And this a really good thing for your identity protection as there is many mechanisms before that email comes to your inbox.
- EOP uses several URL block lists that help detect known malicious links within messages.
- EOP uses a vast list of domains that are known to send spam.
- EOP uses multiple anti-malware engines help to automatically protect our customers at all times.
- EOP inspects the active payload in the message body and all message attachments for malware.
- For recommended values for protection policies, see Recommended settings for EOP and Microsoft Defender for Office 365 security.
- For quick instructions to configure protection policies, see Protect against threats.
See more info on MSFT https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/exchange-online-protection-overview?view=o365-worldwide#eop-features
One of my favorites is ZAP (Zero-Hour Auto purge) It is an detonation chamber for the message, it will initiate and Sandbox environment for testing and when analyzing is done the sandbox is removed completely. When the next message comes, the process will start all over again.
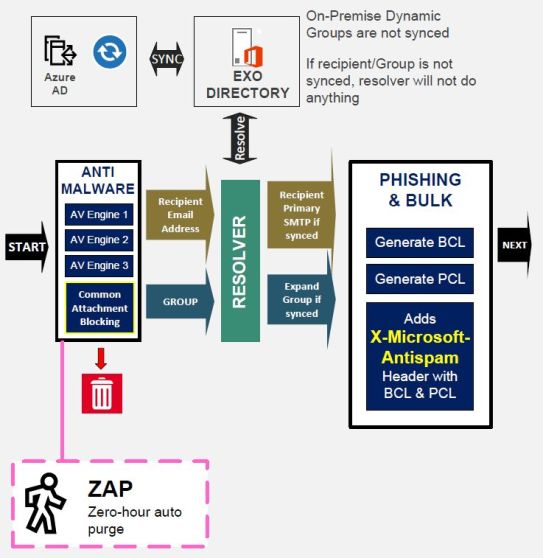
ZAP in actually part of Defender for Office 365 that contains all the security features with Exchange Online Plan 2, but the same sandbox is used for Defender for Endpoints also.

Have you ever used the Sandbox feature in Windows 10 or Windows 11? It’s exactly the same feature, raise a sandbox and delete everything after processing. Windows XP mode was an first version of this one, although it was based on compatibility support rather than security functions.
So, protect your identity with these advises and you will be more safe, but still as I always say. No machine learned algorithm will ever fully protect you unless you are aware of the potential risks out in the wide.
Keep safe out there, from Covid and tech threats.


 RSS - Posts
RSS - Posts