
And time for the second section for my SC-100 study guide:
- Design a logging and auditing strategy to support security operations
- Develop security operations to support a hybrid or multi-cloud environment
- Design a strategy for SIEM and SOAR
- Evaluate security workflows
- Evaluate a security operations strategy for incident management lifecycle
- Evaluate a security operations strategy for sharing technical threat intelligence
Table of Contents
Design a logging and auditing strategy to support security operations
Logging your incidents inside Azure is important. When you have logging configured you can figure out what happened during a breach or more important before it.
Different logs in Azure
| Log category | Log type | Usage | Integration |
|---|---|---|---|
| Activity logs | Control-plane events on Azure Resource Manager resources | Provides insight into the operations that were performed on resources in your subscription. | REST API, Azure Monitor |
| Azure Resource logs | Frequent data about the operation of Azure Resource Manager resources in subscription | Provides insight into operations that your resource itself performed. | Azure Monitor |
| Azure Active Directory reporting | Logs and reports | Reports user sign-in activities and system activity information about users and group management. | Graph API |
| Virtual machines and cloud services | Windows Event Log service and Linux Syslog | Captures system data and logging data on the virtual machines and transfers that data into a storage account of your choice. | Windows (using Azure Diagnostics] storage) and Linux in Azure Monitor |
| Azure Storage Analytics | Storage logging, provides metrics data for a storage account | Provides insight into trace requests, analyzes usage trends, and diagnoses issues with your storage account. | REST API or the client library |
| Network security group (NSG) flow logs | JSON format, shows outbound and inbound flows on a per-rule basis | Displays information about ingress and egress IP traffic through a Network Security Group. | Azure Network Watcher |
| Application insight | Logs, exceptions, and custom diagnostics | Provides an application performance monitoring (APM) service for web developers on multiple platforms. | REST API, Power BI |
| Process data / security alerts | Microsoft Defender for Cloud alerts, Azure Monitor logs alerts | Provides security information and alerts. | REST APIs, JSON |
Azure logs are categorized into the following types:
- Control/management logs provide information about Azure Resource Manager CREATE, UPDATE, and DELETE operations. For more information, see Azure activity logs.
- Data plane logs provide information about events raised as part of Azure resource usage. Examples of this type of log are the Windows event system, security, and application logs in a virtual machine (VM) and the diagnostics logs that are configured through Azure Monitor.
- Processed events provide information about analyzed events/alerts that have been processed on your behalf. Examples of this type are Microsoft Defender for Cloud alerts where Microsoft Defender for Cloud has processed and analyzed your subscription and provides concise security alerts.
Connected Defender solutions
The Connected solutions section includes security solutions that are currently connected to Defender for Cloud. It also shows the health status of each solution.

The status of a partner solution can be:
- Healthy (green) – no health issues.
- Unhealthy (red) – there’s a health issue that requires immediate attention.
- Stopped reporting (orange) – the solution has stopped reporting its health.
- Not reported (gray) – the solution hasn’t reported anything yet and no health data is available. A solution’s status may be unreported if it was connected recently and is still deploying.
Continuous export
You fully customize what will be exported, and where it will go with continuous export. For example, you can configure it so that:
- All high severity alerts are sent to an Azure Event Hub
- All medium or higher severity findings from vulnerability assessment scans of your SQL servers are sent to a specific Log Analytics workspace
- Specific recommendations are delivered to an Event Hub or Log Analytics workspace whenever they’re generated
- The secure score for a subscription is sent to a Log Analytics workspace whenever the score for a control changes by 0.01 or more
| Aspect | Details |
|---|---|
| Release state: | General availability (GA) |
| Pricing: | Free |
| Required roles and permissions: | Security admin or Owner on the resource groupWrite permissions for the target resource.If you’re using the Azure Policy ‘DeployIfNotExist’ policies described below you’ll also need permissions for assigning policiesTo export data to Event Hub, you’ll need Write permission on the Event Hub Policy.To export to a Log Analytics workspace:if it has the SecurityCenterFree solution, you’ll need a minimum of read permissions for the workspace solution: Microsoft.OperationsManagement/solutions/readif it doesn’t have the SecurityCenterFree solution, you’ll need write permissions for the workspace solution: Microsoft.OperationsManagement/solutions/actionLearn more about Azure Monitor and Log Analytics workspace solutions |
| Clouds: |
What data types can be exported?
Continuous export can export the following data types whenever they change:
- Security alerts.
- Security recommendations.
- Security findings. These can be thought of as ‘sub’ recommendations and belong to a ‘parent’ recommendation
- Secure score per subscription or per control.
- Regulatory compliance data.
Deploy with Azure Policy
To deploy your continuous export configurations across your organization, use the supplied Azure Policy ‘DeployIfNotExist’ policies described below to create and configure continuous export procedures.
| Goal | Policy | Policy ID |
|---|---|---|
| Continuous export to Event Hub | Deploy export to Event Hub for Microsoft Defender for Cloud alerts and recommendations | cdfcce10-4578-4ecd-9703-530938e4abcb |
| Continuous export to Log Analytics workspace | Deploy export to Log Analytics workspace for Microsoft Defender for Cloud alerts and recommendations | ffb6f416-7bd2-4488-8828-56585fef2be9 |

Select assign

Open each tab and set the parameters as desired:
- In the Basics tab, set the scope for the policy. To use centralized management, assign the policy to the Management Group containing the subscriptions that will use continuous export configuration.
- In the Parameters tab, set the resource group and data type details.

Log analytics
If you want to analyze Microsoft Defender for Cloud data inside a Log Analytics workspace or use Azure alerts together with Defender for Cloud alerts, set up continuous export to your Log Analytics workspace.

Security Controls v1
Microsoft also has security controls that you can use to design and maintain your logging and monitoring efficiently.
Security audits
When all the logging and monitoring is done, you have to maintain the state with audits.
- Improve secure score in Microsoft Defender for Cloud.
- Use an industry standard benchmark to evaluate your organizations current security posture.
- Perform regular internal and external compliance audits, including regulatory compliance attestations.
- Review the policy requirements.
Or use can use the excellent tool called AzGovViz by Julian Hayward
It will allow you to get a holistic view of your security settings.
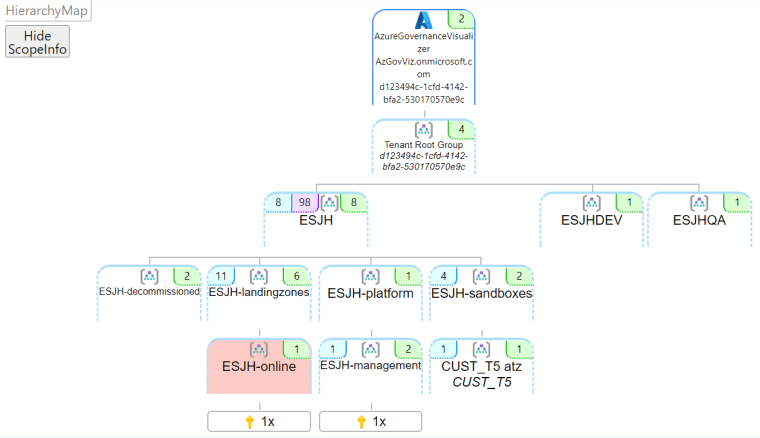
And the policies your have applied to your resources

You can export the reports to:
- CSV file
- HTML file
- Markdown file
- JSON folder format
ASB v3 (Azure Security Benchmark)
- Mappings to the industry frameworks PCI-DSS v3.2.1 and CIS Controls v8 are added in addition to the existing mappings to CIS Controls v7.1 and NIST SP800-53 Rev4.
- Refining the control guidance to be more granular and actionable, e.g., security guidance is now divided into two separate parts, Security Principle and Azure Guidance. Security Principle is the “what”, explaining the control at the technology-agnostic level; Azure Guidance is focused on the “how”, elaborating on the relevant technical features and ways to implement the controls in Azure.
- The addition of new control(s), e.g., DevOps Security as a new control family which also includes topics such as threat modeling and software supply chain security. Key and certificate management was introduced to recommend key and certificate management best practices in Azure.
Recommendations
- ASB ID: The Azure Security Benchmark ID that corresponds to the recommendation.
- CIS Controls v8 ID(s): The CIS Controls v8 control(s) that correspond to the recommendation.
- CIS Controls v7.1 ID(s): The CIS Controls v7.1 control(s) that correspond to the recommendation (not available in the web due to the formatting reason).
- PCI-DSS v3.2.1 ID(s): The PCI-DSS v3.2.1 control(s) that correspond to the recommendation.
- NIST SP 800-53 r4 ID(s): The NIST SP 800-53 r4 (Moderate and High) control(s) that correspond to this recommendation.
- Security Principle: The recommendation focused on the “what”, explaining the control at the technology-agnostic level.
- Azure Guidance: The recommendation focused on the “how”, explaining the Azure technical features and implementation basics.
- Implementation and addition context: The implementation details and other relevant context which links to the Azure service offering documentation articles.
- Customer Security Stakeholders: The security functions at the customer organization who may be accountable, responsible, or consulted for the respective control. It may be different from organization to organization depending on your company’s security organization structure, and the roles and responsibilities you set up related to Azure security.
Develop security operations to support a hybrid or multi-cloud environment
Defender for Cloud
For multi-cloud Microsoft has Defender for Cloud. It’s has two sides; Cloud Workload Protection Platform (CWPP) and Cloud Security Posture Management (CSPM).
Once you enable Defender for Cloud it will
- Generate a secure score for your subscriptions based on an assessment of your connected resources compared with the guidance in Azure Security Benchmark. Use the score to understand your security posture, and the compliance dashboard to review your compliance with the built-in benchmark. When you’ve enabled the enhanced security features, you can customize the standards used to assess your compliance, and add other regulations (such as NIST and Azure CIS) or organization-specific security requirements. You can also apply recommendations, and score based on the AWS Foundational Security Best practices standards.
- Provide hardening recommendations based on any identified security misconfigurations and weaknesses. Use these security recommendations to strengthen the security posture of your organization’s Azure, hybrid, and multi-cloud resources.
It will protect native resources inside Azure:
- Azure PaaS services – Detect threats targeting Azure services including Azure App Service, Azure SQL, Azure Storage Account, and more data services. You can also perform anomaly detection on your Azure activity logs using the native integration with Microsoft Defender for Cloud Apps (formerly known as Microsoft Cloud App Security).
- Azure data services – Defender for Cloud includes capabilities that help you automatically classify your data in Azure SQL. You can also get assessments for potential vulnerabilities across Azure SQL and Storage services, and recommendations for how to mitigate them.
- Networks – Defender for Cloud helps you limit exposure to brute force attacks. By reducing access to virtual machine ports, using the just-in-time VM access, you can harden your network by preventing unnecessary access. You can set secure access policies on selected ports, for only authorized users, allowed source IP address ranges or IP addresses, and for a limited amount of time.
Inside on-premises (Azure ARC)
You can add Defender for Cloud capabilities to your hybrid cloud environment to protect your non-Azure servers.

Amazon


Once servers are onboarded you can use Defender for Cloud to generate an inventory.

Checklist for Azure security
| Checklist Category | Description |
|---|---|
Security Roles & Access Controls | Use Azure role-based access control (Azure RBAC) to provide user-specific that used to assign permissions to users, groups, and applications at a certain scope. |
Data Collection & Storage | Use Management Plane Security to secure your Storage Account using Azure role-based access control (Azure RBAC).Data Plane Security to Securing Access to your Data using Shared Access Signatures (SAS) and Stored Access Policies.Use Transport-Level Encryption – Using HTTPS and the encryption used by SMB (Server message block protocols) 3.0 for Azure File Shares.Use Client-side encryption to secure data that you send to storage accounts when you require sole control of encryption keys.Use Storage Service Encryption (SSE) to automatically encrypt data in Azure Storage, and Azure Disk Encryption to encrypt virtual machine disk files for the OS and data disks.Use Azure Storage Analytics to monitor authorization type; like with Blob Storage, you can see if users have used a Shared Access Signature or the storage account keys.Use Cross-Origin Resource Sharing (CORS) to access storage resources from different domains. |
Security Policies & Recommendations | Use Microsoft Defender for Cloud to deploy endpoint solutions.Add a web application firewall (WAF) to secure web applications.Use a firewall from a Microsoft partner to increase your security protections.Apply security contact details for your Azure subscription; this the Microsoft Security Response Center (MSRC) contacts you if it discovers that your customer data has been accessed by an unlawful or unauthorized party. |
Identity & Access Management | Synchronize your on-premises directory with your cloud directory using Azure AD.Use Single Sign-On to enable users to access their SaaS applications based on their organizational account in Azure AD.Use the Password Reset Registration Activity report to monitor the users that are registering.Enable multi-factor authentication (MFA) for users.Developers to use secure identity capabilities for apps like Microsoft Security Development Lifecycle (SDL).Actively monitor for suspicious activities by using Azure AD Premium anomaly reports and Azure AD identity protection capability. |
Ongoing Security Monitoring | Use Malware Assessment Solution Azure Monitor logs to report on the status of antimalware protection in your infrastructure.Use Update assessment to determine the overall exposure to potential security problems, and whether or how critical these updates are for your environment.The Identity and Access provide you an overview of useruser identity state,number of failed attempts to sign in,the user’s account that were used during those attempts, accounts that were locked outaccounts with changed or reset passwordCurrently number of accounts that are logged in. |
Microsoft Defender for Cloud detection capabilities | Use detection capabilities, to identify active threats targeting your Microsoft Azure resources.Use integrated threat intelligence that looks for known bad actors by leveraging global threat intelligence from Microsoft products and services, the Microsoft Digital Crimes Unit (DCU), the Microsoft Security Response Center (MSRC), and external feeds.Use Behavioral analytics that applies known patterns to discover malicious behavior.Use Anomaly detection that uses statistical profiling to build a historical baseline. |
Developer Operations (DevOps) | Infrastructure as Code (IaC) is a practice, which enables the automation and validation of creation and teardown of networks and virtual machines to help with delivering secure, stable application hosting platforms.Continuous Integration and Deployment drive the ongoing merging and testing of code, which leads to finding defects early.Release Management Manage automated deployments through each stage of your pipeline.App Performance Monitoring of running applications including production environments for application health and customer usage help organizations form a hypothesis and quickly validate or disprove strategies.Using Load Testing & Auto-Scale we can find performance problems in our app to improve deployment quality and to make sure our app is always up or available to cater to the business needs. |
Design a strategy for SIEM and SOAR
What Sentinel is?
Azure Sentinel is a cloud-based Security Information Event Management (SIEM) and Security Orchestration Automated Response (SOAR) platform that draws on cloud-native security info, threat intelligence, and other Azure technologies.
What is SIEM?
A SIEM is made up of two components. The Security Event Manager (SEM), which monitors real-time events as they take place on your network, comes first. The Security Information Manager (SIM), the second option, is in charge of longer-term data retention and analysis. Together, these two components enable a SIEM to manage events as they occur and produce reports and trend analysis over time, making it a useful addition to any network.
What is SOAR?
The “Orchestration” component where all of the different parts come together and function as a unit under centralized control and guidance. It resembles the playground supervisor who ensures that everyone behaves themselves in the sandbox. The action-driven element that carries out the actual work in accordance with the workflows and procedures necessary to complete a security task is the automation component. Automating the end of a user session, alerting a message platform, or changing a status indication are a few examples. The Response component responds to an input, in this case possibly the outcome of information obtained from a SIEM or a third-party tool.
Evaluate alerts and incidents in Azure Sentinel
Prerequisites
- You’ll only be able to investigate the incident if you used the entity mapping fields when you set up your analytics rule. The investigation graph requires that your original incident includes entities.
- If you have a guest user that needs to assign incidents, the user must be assigned the Directory Reader role in your Azure AD tenant. Regular (non-guest) users have this role assigned by default.
Simulating data with Azure Sentinel Training Lab environment
If you training and you want to simulate content for Sentinel, you could use example Microsoft’s own Azure Sentinel Training Lab environment
What does it include?
This training package includes pre-recorded data that will be ingested into the selected Microsoft Sentinel Workspace. Don’t worry about ingestion costs, the sample data is only 20 MBs in size! This pre-recorded data will land in the following custom log tables: SecurityEvent_CL, SigninLogs_CL, OfficeActivity_CL, AzureActivity_CL, Cisco_Umbrella_dns_CL.
On top of this ingested data, the solution deploys several artifacts to simulate scenarios that showcase various Microsoft Sentinel features. These artifacts are:
- 3 x Analytics Rules
- 2 x Hunting queries
- 2 x Parsers
- 1 x Workbook
- 1 x Playbook
How to?

Choose your Log analytics workspace

Give a name for the Investigations insights

So cool

and define a Playbook name

Before creating the rule it will ask for Your real email and phone number, no worries, you won’t be billed, yet.

And let the provisioning begin

Analyzing the incidents
And now I have home made incidents inside my Sentinel. Looks bad but feels good.
First from the Overview screen you can see the incidents and open recent incidents

You can also see those incidents from Workbooks

And from incidents, click the incident and View full details

From action you can do the following, creating a Teams channel is really cool. This ways You could collaborate with the whole responsive team.

Evaluate security workflows
Security workflows can be created with a combination of Defender for cloud and Logic apps.
| Required roles and permissions: | Security admin role or Owner on the resource group Must also have write permissions for the target resource To work with Azure Logic Apps workflows, you must also have the following Logic Apps roles/permissions: – Logic App Operator permissions are required or Logic App read/trigger access (this role can’t create or edit logic apps; only run existing ones) – Logic App Contributor permissions are required for Logic App creation and modification If you want to use Logic App connectors, you may need other credentials to sign in to their respective services (for example, your Outlook/Teams/Slack instances) |
Basically you create a Logic app for automating the action based on alerts, recommendation or compliance standards.

Some of the pre-built actions are:
- Create an automated incident report in another system, filling in fields from the active alert
- Email a distribution group with details about the active alert(s)
- Send a notification to a Teams or Slack channel

There’s even predefined apps to accomplish this.

Evaluate a security operations strategy for incident management lifecycle
Security operations (SecOps)
Microsoft has excellent resources for people in Security roles in different stages.
New-to-role
| Topic | Resource |
|---|---|
| SecOps planning for incident response | Incident response planning for preparing your organization for an incident. |
| SecOps incident response process | Incident response process for best practices on responding to an incident. |
| Incident response workflow | Example incident response workflow for Microsoft 365 Defender |
| Periodic security operations | Example periodic security operations for Microsoft 365 Defender |
| Investigation for Microsoft Sentinel | Incidents in Microsoft Sentinel |
| Investigation for Microsoft 365 Defender | Incidents in Microsoft 365 Defender |
Experienced security analyst
| Topic | Resource |
|---|---|
| Microsoft Sentinel | How to investigate incidents |
| Microsoft Defender for Cloud (Azure resources) | How to investigate alerts |
| Microsoft 365 Defender | How to investigate incidents |
| Security operations establishment or modernization | Azure Cloud Adoption Framework articles for SecOps and SecOps functions |
| Microsoft security best practices | How to best use your SecOps center |
| Incident response playbooks | Overview at https://aka.ms/IRplaybooks – Phishing – Password spray – App consent grant |
| SOC Process Framework | Microsoft Sentinel |
| MSTICPy and Jupyter Notebooks | Microsoft Sentinel |
Azure Security Benchmark has excellent steps for incident lifecycle management. There is 7 different stages from detection to learning lessons.
Collaborate in Microsoft Teams (Preview)
Excellent solution to collaborate when an incident happens is Sentinel integration with Teams.
Required permissions
In order to create teams from Microsoft Sentinel:
- The user creating the team must have Incident write permissions in Microsoft Sentinel. For example, the Microsoft Sentinel Responder role is an ideal, minimum role for this privilege.
- The user creating the team must also have permissions to create teams in Microsoft Teams.
- Any Microsoft Sentinel user, including users with the Reader, Responder, or Contributor roles, can gain access to the created team by requesting access.
Settings for your incident team
- Team name: Automatically defined as the name of your incident. Modify the name as needed so that it’s easily identifiable to you.
- Team description: Enter a meaningful description for your incident team.
- Add groups and members: Select one or more Azure AD users and/or groups to add to your incident team. As you select users and groups, they will appear in the Selected groups and users: list below the Add groups and members list.

Evaluate a security operations strategy for sharing technical threat intelligence
Security responsibilities from CAF model

Metrics
- Mean time to acknowledge (MTTA): Responsiveness is one of the few elements SecOps has more direct control over. Measure the time between an alert, like when the light starts to blink, and when an analyst sees that alert and begins the investigation. Improving this responsiveness requires that analysts don’t waste time investigating false positives. It can be achieved with ruthless prioritization, ensuring that any alert feed that requires an analyst response must have a track record of 90 percent true positive detections.
- Mean time to remediate (MTTR): Effectiveness of reducing risk measures the next period of time. That period is the time the analyst begins the investigation to when the incident is remediated. MTTR identifies how long it takes SecOps to remove the attacker’s access from the environment. This information helps identify where to invest in processes and tools to help analysts reduce risk.
- Incidents remediated (manually or with automation): Measuring how many incidents are remediated manually and how many are resolved with automation is another key way to inform staffing and tool decisions.
- Escalations between each tier: Track how many incidents escalated between tiers. It helps ensure accurate tracking of the workload to inform staffing and other decisions. For example, so that work done on escalated incidents isn’t attributed to the wrong team.

SecOps teams
- Triage (tier 1): The first line of response for security incidents. Triage is focused on the high-volume processing of alerts, and typically generated by automation and tools. The triage processes solve for most of common incident types and resolve them within the team. More complex incidents, or incidents that haven’t been seen and resolved before should be escalated to tier 2.
- Investigation (tier 2): Focused on incidents that require further investigation, often requiring correlation of data points from multiple sources. This investigation tier looks to provide repeatable solutions to issues escalated to them. It then enables tier 1 to resolve later recurrences of that issue type. Tier 2 will also respond to alerts against business critical systems, to reflect the severity of the risk and the need to act quickly.
- Hunt (tier 3): Focused primarily on proactive hunting for highly sophisticated attack processes and developing guidance to the wider teams for maturing security controls as a result. The tier 3 team also acts as an escalation point for major incidents in to support forensic analysis and response.
Top 10 for Azure security

Things to remember
Cloud Adoption Framework by hearth. There is many excellent best practices covered inside CAF model.

Different areas

And their roles
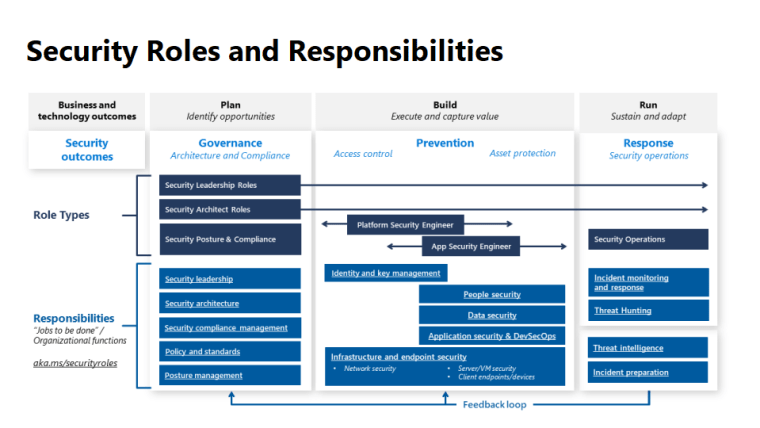
Different frameworks followed
- Zero trust: Microsoft believes all security disciplines should follow the zero-trust principles of assume breach, verify explicitly, and use least privilege access. These principles underpin any sound security strategy and also must be balanced with business enablement goals. The first and most visible part of zero trust is in access control, so it’s highlighted in the description of access control security discipline.
- The Open Group: These security disciplines map closely to the zero-trust components in the core principles white paper published by The Open Group, where Microsoft actively participates. The one notable exception is that Microsoft elevated the discipline of innovation security so that DevSecOps is a top-level element because of how new, important, and transformative this discipline is for many organizations.
- NIST cybersecurity framework: For organizations that use the NIST cybersecurity framework, we have highlighted bold text where the framework most closely maps. Modern access control and DevSecOps map broadly to the full spectrum of the framework, so those items aren’t noted individually.
And how to fulfil them technically with Defender for Cloud automation and Sentinel trigger


 RSS - Posts
RSS - Posts