
Time for first half of section 9 in my SC-300 study guide and covering the following:
- plan and implement security defaults
- plan conditional access policies
- implement conditional access policy controls and assignments (targeting, applications,
- and conditions)
- testing and troubleshooting conditional access policies
- implement application controls
- implement session management
Table of Contents
Plan and implement security defaults
Before anything create Break the glass Global admin account! If anything goes wrong you still have means to access.
Emergency access accounts are:
- Assigned Global Administrator rights in Azure AD
- Aren’t used on a daily basis
- Are protected with a long complex password

What it will apply to Your tenant?
- Requiring all users to register for Azure AD Multi-Factor Authentication.
- Requiring administrators to do multi-factor authentication.
- Blocking legacy authentication protocols.
- Requiring users to do multi-factor authentication when necessary.
- Protecting privileged activities like access to the Azure portal.
Unified Multi-Factor Authentication registration
All users in your tenant must register for multi-factor authentication (MFA) in the form of the Azure AD Multi-Factor Authentication. Users have 14 days to register for Azure AD Multi-Factor Authentication by using the Microsoft Authenticator app. After the 14 days have passed, the user can’t sign in until registration is completed. A user’s 14-day period begins after their first successful interactive sign-in after enabling security defaults.
Protecting administrators
After registration with Azure AD Multi-Factor Authentication is finished, the following Azure AD administrator roles will be required to do extra authentication every time they sign in:
- Global administrator
- Application administrator
- Authentication administrator
- Billing administrator
- Cloud application administrator
- Conditional Access administrator
- Exchange administrator
- Helpdesk administrator
- Password administrator
- Privileged authentication administrator
- Security administrator
- SharePoint administrator
- User administrator
Protecting all users
We tend to think that administrator accounts are the only accounts that need extra layers of authentication. Administrators have broad access to sensitive information and can make changes to subscription-wide settings. But attackers frequently target end users.
Blocking legacy authentication
To give your users easy access to your cloud apps, Azure AD supports various authentication protocols, including legacy authentication. Legacy authentication is a term that refers to an authentication request made by:
- Clients that don’t use modern authentication (for example, an Office 2010 client).
- Any client that uses older mail protocols such as IMAP, SMTP, or POP3.
Protecting privileged actions
After you enable security defaults in your tenant, any user accessing the following services must complete multi-factor authentication:
- Azure portal
- Azure PowerShell
- Azure CLI
When to disable?
If You have Security defaults, You have to disable them before enabling Conditional Access policies.
What is Conditional access?
Conditional Access is based on conditions for a location, devices used, risks discovered.
Here is an excellent picture from Microsoft which explain the flow.

Licensing
You need at least Azure AD Premium P1 to enable Conditional Access.
What could be enabled?
Microsoft currently has a Preview feature for CA templates. These will show many examples on what You can enable.
Identity templates

Device templates

Remember that the Preview features aren’t coming to certification Exams. Once this feature is Generally Available it will be a beautiful addition.
Terms of use
Terms of use gives the CA users an choice to accept the terms You provide. Excellent feature for governance.

When You create an policy, you can require Terms of use you created.

GPS locations
You can now create GPS locations to Named locations.

When the location condition of a Conditional Access policy is configured, users will be prompted by the Authenticator app to share their GPS location.
How to Enable MFA with Conditional Access?
Conditional Access and MFA is much more convenient than MFA by itself. There is policies the user will get if they fall to the scope.
CA policies
Search for Conditional Access inside Azure portal.

Once there, create a new policy

You will se the policy editor, give a name and choose Users or workloads.
In here You can choose to include on exclude users, roles or groups. A nice option is also to Enable something with Conditional Access only to Guest and External users that reside or will be invited to Your tenant.

I will keep it simple in my example and choose only one user. But You really could fiddle around with these an make Your own kind of policy.

Next You can choose Cloud Apps or actions. In my example I will choose Office 365 which includes all Office 365 Services.
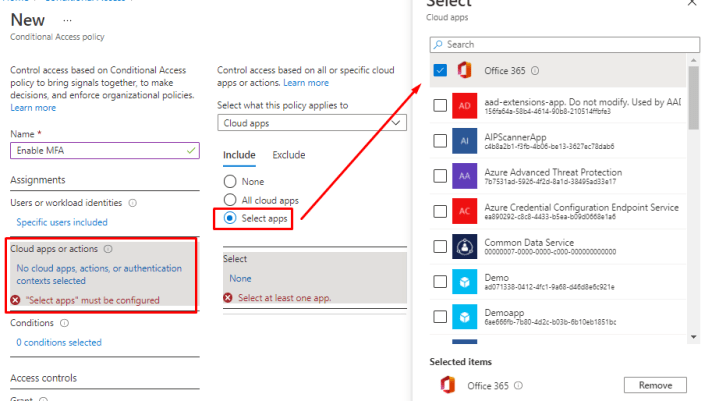
For the user actions You could choose the following.

User Actions
User actions
User actions are tasks that can be performed by a user. Currently, Conditional Access supports two user actions:
- Register security information: This user action allows Conditional Access policy to enforce when users who are enabled for combined registration attempt to register their security information. More information can be found in the article, Combined security information registration.
- Register or join devices: This user action enables administrators to enforce Conditional Access policy when users register or join devices to Azure AD. It provides granularity in configuring multi-factor authentication for registering or joining devices instead of a tenant-wide policy that currently exists. There are three key considerations with this user action:
Require multi-factor authenticationis the only access control available with this user action and all others are disabled. This restriction prevents conflicts with access controls that are either dependent on Azure AD device registration or not applicable to Azure AD device registration.Client apps,Filters for devicesandDevice stateconditions aren’t available with this user action since they’re dependent on Azure AD device registration to enforce Conditional Access policies.- When a Conditional Access policy is enabled with this user action, you must set Azure Active Directory > Devices > Device Settings –
Devices to be Azure AD joined or Azure AD registered require Multi-Factor Authenticationto No. Otherwise, the Conditional Access policy with this user action isn’t properly enforced. More information about this device setting can found in Configure device settings.
Conditions
Then choose Conditions, in here You will define the conditions that will trigger the policy.

In example if the user has risk of Medium they would be Enforced for the policy.

In the Grant section You will define to block the user matching the policy or Grant with controls.
To keep it simple I will choose only require MFA

In Sessions You will have the following. In here You can control App restrictions, disable persistent sessions and Continuous Access Evaluation (CAE) but You really shouldn’t. These are excellent and relatively new features inside Conditional Access policies.

If you want to learn more about both, here’s my previous posts.Conditional Access – CAE and Resilience defaultsIn the beginning of this month I wrote about CAE and and now it came Globally available. It was there but now it’s gone and the only option you have is to disable or enforce it. So what is Continuous Access Evaluation? Continuous Access Evaluation (CAE) allows access tokens to be revoked based on critical.
Service principals
Now you can also choose Workload identities (Service principal) to policy scope not only users and groups. The action currently supported is Block. This is currently a Preview feature and therefore not coming to the test if You take it soon.

Authentication methods
| Method | Security defaults | Conditional Access |
|---|---|---|
| Notification through mobile app | X | X |
| Verification code from mobile app or hardware token | X** | X |
| Text message to phone | X | |
| Call to phone | X | |
| App passwords | X*** |
- ** Users may use verification codes from the Microsoft Authenticator app but can only register using the notification option.
- *** App passwords are only available in per-user MFA with legacy authentication scenarios only if enabled by administrators.
Troubleshooting
Report-Only
And finally there is option to Enable or Report. With reporting You will get information about how it would be affecting users.

But remember this, depending on Your setup Your user could get prompts even in Report-Only mode.

If You want to access the logs for reporting, they can be found under sign-in logs.

You also have a What If so see what will happen if You enable the policy.
What If

Sign-in logs

Sign-logs activity details

From here you can see the details of CA policy processing.

Conditional Access error codes
| Sign-in Error Code | Error String |
|---|---|
| 53000 | DeviceNotCompliant |
| 53001 | DeviceNotDomainJoined |
| 53002 | ApplicationUsedIsNotAnApprovedApp |
| 53003 | BlockedByConditionalAccess |
| 53004 | ProofUpBlockedDueToRisk |
Things to remember
Licensing
Conditional Access is available in the following licensing options:
- Azure AD Premium P1
- Azure AD Premium P2
Security defaults
Security Defaults are enabled by default and has to be disable before enabling Conditional Access.
What it will apply to Your tenant:
- Requiring all users to register for Azure AD Multi-Factor Authentication.
- Requiring administrators to do multi-factor authentication.
- Blocking legacy authentication protocols.
- Requiring users to do multi-factor authentication when necessary.
- Protecting privileged activities like access to the Azure portal.
14 days grace period to register for Azure AD Multi-Factor Authentication
Conditional Access
No grace period to enable MFA.
Conditional Access has User and Sign-in risk policies.
Conditional access support GPS locations, for this have to enable MS authenticator location.
Authentication methods supported by CA and Security defaults

 RSS - Posts
RSS - Posts