Second half of section 9 and going down with:
- implement and manage a user risk policy
- implement and manage sign-in risk policy
- implement and manage MFA registration policy
- monitor, investigate and remediate elevated risky users
Table of Contents
What is Identity Protection?
Identity Protection uses the learnings Microsoft has acquired from their position in organizations with Azure AD, the consumer space with Microsoft Accounts, and in gaming with Xbox to protect your users. Microsoft analyses 6.5 trillion signals per day to identify and protect customers from threats.
The signals generated by and fed to Identity Protection, can be further fed into tools like Conditional Access to make access decisions, or fed back to a security information and event management (SIEM) tool for further investigation based on your organization’s enforced policies.
Permissions needed
| Role | Can do | Can’t do |
|---|---|---|
| Global administrator | Full access to Identity Protection | |
| Security administrator | Full access to Identity Protection | Reset password for a user |
| Security operator | View all Identity Protection reports and Overview blade Dismiss user risk, confirm safe sign-in, confirm compromise | Configure or change policies Reset password for a user Configure alerts |
| Security reader | View all Identity Protection reports and Overview blade | Configure or change policies Reset password for a user Configure alerts Give feedback on detections |
Licensing requirements
| Capability | Details | Azure AD Free / Microsoft 365 Apps | Azure AD Premium P1 | Azure AD Premium P2 |
|---|---|---|---|---|
| Risk policies | User risk policy (via Identity Protection) | No | No | Yes |
| Risk policies | Sign-in risk policy (via Identity Protection or Conditional Access) | No | No | Yes |
| Security reports | Overview | No | No | Yes |
| Security reports | Risky users | Limited Information. Only users with medium and high risk are shown. No details drawer or risk history. | Limited Information. Only users with medium and high risk are shown. No details drawer or risk history. | Full access |
| Security reports | Risky sign-ins | Limited Information. No risk detail or risk level is shown. | Limited Information. No risk detail or risk level is shown. | Full access |
| Security reports | Risk detections | No | Limited Information. No details drawer. | Full access |
| Notifications | Users at risk detected alerts | No | No | Yes |
| Notifications | Weekly digest | No | No | Yes |
| MFA registration policy | No | No | Yes |
How to Enable?
Open https://portal.azure.com and search for Azure AD Identity

Under the page You will find the following which will be covered in the examples.

Implement and manage a user risk policy
Inside User risk policy You can define User risk from Low to High and different approaches to these levels.

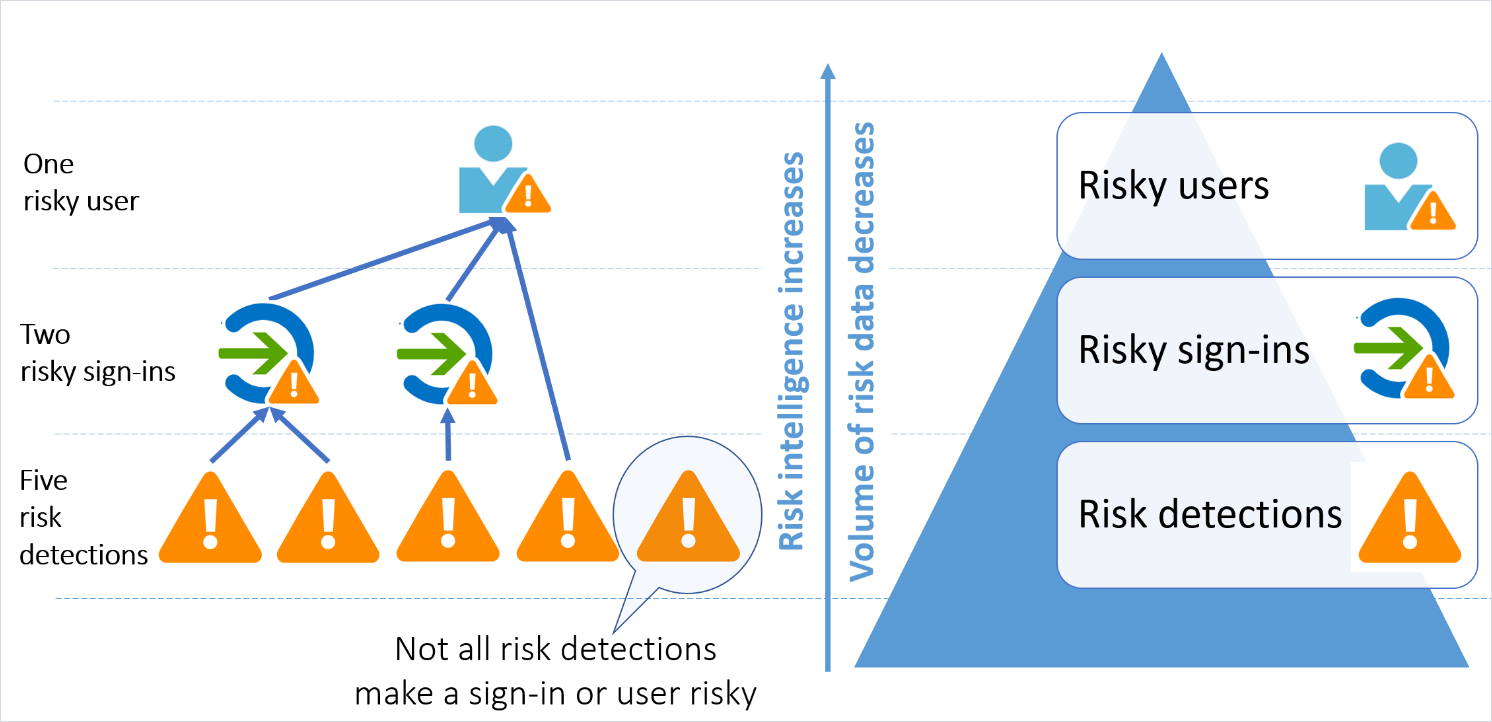
What is a risk?
Risk types and detection
Risk can be detected at the User and Sign-in level and two types of detection or calculation Real-time and Offline.
Real-time detections may not show up in reporting for five to 10 minutes. Offline detections may not show up in reporting for 48 hours.

User-linked detections
Sign-in risk
Other risk detections
After Your specified User risk level is reached, You can specify to block login, allow login and allow login and force password change.

Then You have an option to Enforce the policy.

Implement and manage sign-in risk policy
In the Sign-in risk page You can block access or allow access but require MFA again.

Implement and manage MFA registration policy
You can enforce MFA registration with MFA registration policy. There is a 14 days grace period where the user can skip the registration.

Monitor, investigate and remediate elevated risky users
Reporting
In the Risky user report You can confirm users confirmed or dismiss the risks

Notifying
In the Notify page You can define new recipients for emails, download the users that have notify enabled and enable alert on only at specified level and above.

Main screen
If we go back to main page, You will see the risk by default inside 30 days.

And You can extend the time to 90 days.

Summary of risk types
User risk
The risk of an individual user is calculated offline based on Microsoft’s internal and external threat intelligence sources. Researchers, law enforcement professionals, and Microsoft security teams are among these sources. An individual’s risk of being compromised is determined by their behavior. A user’s risk is determined offline.
Leaked credentials
The Microsoft leaked credentials service acquires credentials on the dark web, paste sites, password dumps and more. All these passwords are checked against the users’ current credentials to find a match.
Azure AD threat intelligence
The activity of the user is compared with the normal activity for the given user. Unusual activity or activity that is consistent with known attach patterns will be flagged.
Sign-in risk
A Sign-in risk is calculated offline or in real-time and represents the probability that an authentication request isn’t legit. Unlike User risk, there are more detection types in place.
Admin confirmed user compromised
An admin can confirm a user is compromised when he or she chooses to confirm a user compromised in the risky users portal (or by using Microsoft Graph).
Atypical travel
Offline detection type ‘atypical travel’ identifies sign-ins from geographically distant locations. By analyzing the user’s past behavior, a machine learning algorithm can identify risk. In the case of impossible travel time, the user credentials are being used by a different person.
Atypical travel has a learning period of 14 days or 10 logins (whatever comes first) in which it learns the sign-in behavior of a new user. This results in false positives (regular locations within the organization, VPNs) being ignored.
Anonymous IP Address
Anonymous is a realtime detection type that identifies sign-ins from IP addresses that are used by VPN services or anonymous browsers like Tor. These services are typically used by people with malicious intent.
Unfamiliar sign-in properties
An unfamiliar sign-in property is a type of real-time detection that compares sign-ins with previous sign-ins. It is calculated in real-time while logged on by looking at IP address, location, known/past IP address, IP carriers, and browsing sessions.
Unfamiliar sign-in properties have a dynamic learning period. A user will be in learning mode for a minimum duration of five days until the algorithm has enough information about the user’s behavior.
Malware linked IP address
Malware linked IP address is an offline detection type that will trigger when a sign-in from an IP address that is known to actively communicate with a bot server.
Malicious IP address
There is an offline detection type called malicious IP address, which indicates signing in from an IP address that has a high logon failure rate due to invalid credentials.
Things to remember
Licensing:
Azure AD Free / Microsoft 365 Apps on has reporting capabilities.
Azure AD Premium P1 also has reporting capabilities for Risky detections.
Azure AD Premium P2 has all features.
Types of risks:
User Risk has Leaked credentials or is discovered by Azure Threat intelligence.
Sign-in risk, atypical travel, unfamiliar location etc.
Reports and notifies go to Global Admins by default
MFA registration policy has 14 days of grace period.


 RSS - Posts
RSS - Posts