
And then to the last portion of section 12 in my SC-300 study guide. Today is the turn for:
- integrate custom SaaS apps for SSO
- configure pre-integrated (gallery) SaaS apps
- implement application user provisioning
Table of Contents
Integrate custom SaaS apps for SSO

Create Your own.

Add a Non-gallery app

Once deployed, open SSO and add SAML

and edit.

Add the following
Identifier (Entity Id): urn:microsoft:adfs:claimsxray
Reply URL (Assertion Consumer Service URL): https://adfshelp.microsoft.com/ClaimsXray/TokenResponse
| Identifier (Entity ID) | Uniquely identifies the application. Azure AD sends the identifier to the application as the Audience parameter of the SAML token. The application is expected to validate it. |
| Reply URL | Specifies where the application expects to receive the SAML token. The reply URL is also referred to as the Assertion Consumer Service (ACS) URL |

and save.

And don’t test yet.

Then add a user to the application.


AAD Connect and extension attributes

Let’s try out with EmployeeID

On-premises AD Account
Add the ID for a user

Transformation rules

Sync the attributes.
Manage claims

blaablaa

Myapplications.microsoft.com

And it will open the following page.

And under Claims you will the My_EmployeeID

Revoke sessions
And if we go revoke the users sessions.

They have to sign-in again and the token is generated again.

Conditional access
Policy
Settings up the following policy and only for the particular user.

We can see Conditional access policies under Enterprise applications.

End-user experience
Let’s see what happens when it’s enabled and user open the application.

and done.

And then the end-users have to agree to Terms of Use, wuhuu!

Quick tip!
The Claims X-ray that I used in this example is part of ADFS help toolkit. The is Online and Offline tools that You could use to debug or find out possibilities with claims.


Configure pre-integrated (gallery) SaaS apps
Amazon Web Services
Go to add another application and add from gallery. I will use AWS in my demo.

It support SSO and Provisioning

Once a get the application created, you will see it has all the claims and setups ready.


End-user experience
Once again go to myapplications.microsoft.com and you will find AWS there.

Implement application user provisioning
Many organizations rely on software as a service (SaaS) applications such as ServiceNow, Zscaler, and Slack for end-user productivity. Historically IT staff have relied on manual provisioning methods such as uploading CSV files, or using custom scripts to securely manage user identities in each SaaS application. These processes are error prone, insecure, and hard to manage.
Azure Active Directory (Azure AD) automatic user provisioning simplifies this process by securely automating the creation, maintenance, and removal of user identities in SaaS applications based on business rules. This automation allows you to effectively scale your identity management systems on both cloud-only and hybrid environments as you expand their dependency on cloud-based solutions.
How enable role provisioning from AWS to Azure
Download metadata
Get the federation metadata from Enterprise application, you will need it soon enough.

Open https://console.aws.amazon.com/singlesignon

Create AWS organization
Create an AWS organization (it’s free)

When create You will be taken to the following page.

Identity source is optional to setup.
Choosing an identity source determines where AWS SSO looks for users and groups that need SSO access. By default, you get an AWS SSO store for quick and easy user management. Optionally, you can also connect an external identity provider or connect an AWS Managed Microsoft AD directory with your self-managed Active Directory.
AWS SSO provides users in this identity source with a personalized user portal from which they can easily launch multiple AWS accounts or cloud applications. Users sign in to the portal using their corporate credentials or with credentials they set up in AWS SSO. Once they sign in, they have one-click access to all applications and AWS accounts that you have previously authorized.
AWS IAM


Give it a name and upload the metadata file from your Enterprise application that we got in the beginning.

Assign a role

Create a new role

Choose SAML 2.0 federation and “Allow programmatic and AWS Management Console access”

Then to permissions and choose AdministratorAccess

In the review screen, give it a name.

Then policies and create policy

Choose JSON

And add the following.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "iam:ListRoles" ], "Resource": "*" } ] } |
Add a name and select create policy

Adding users
Open users and add a user

Create a user and choose access key as credential type.

Next attach permissions created earlier.

And create the new admin user.

After created you will see the Access key and secret for the user.

Azure AD enterprise app
You will then copy these keys to the AWS Enterprise application.

And You can now start provisioning if needed.

And when it’s done, we will have the role we create to AWS.

Note that the provisioning will run every 40 minutes but You can start it manually if needed.
Automatic user provisioning from AAD to AWS
You can also implement on-premises AD with AWS and other OICD and SAML compliant sources.

Press next and you will see download metadata

Create a new application
Find the following and create.

Then go back to Azure AD and upload Your metadata

And download from Azure AD and upload to AWS.

Upload and config change.

And click enable in AWS.

And take note of the endpoint and token.

And then back to Azure AD and add the URL and access token under the application. This is a preview feature, so things could change when going Globally available.

Attribute mapping
Under mapping you will find that users and group will be automatically created to AWS.

And the following operations are supported.

And you can remove attribute mappings if needed.

Under advanced you will see the supported attributes and can build your own expressions.

End-user experience
When user is assigned to the application, they will see it inside My apps portal

And user will logon with their own credentials to AWS.
AWS portal
You can see from Azure AD that users and groups are synced.
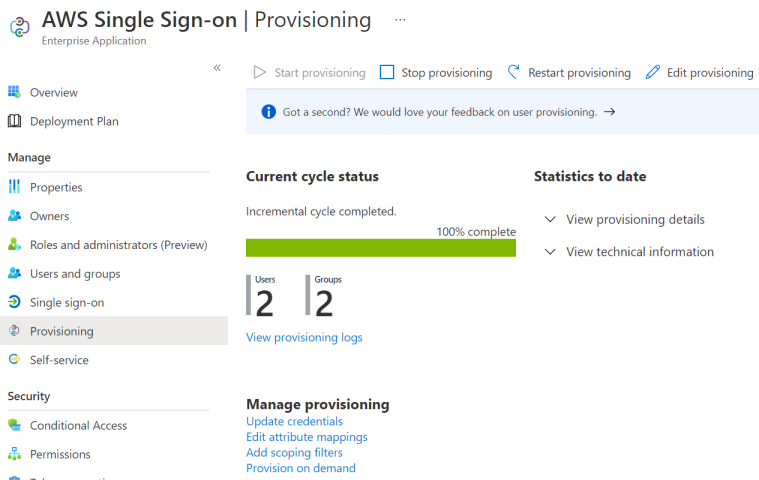
And from AWS you can see the user has been created by SCIM

Provisioning users to AAD with SCIM

Components of system
- HCM system: Applications and technologies that enable Human Capital Management process and practices that support and automate HR processes throughout the employee lifecycle.
- Azure AD Provisioning Service: Uses the SCIM 2.0 protocol for automatic provisioning. The service connects to the SCIM endpoint for the application, and uses the SCIM user object schema and REST APIs to automate provisioning and de-provisioning of users and groups.
- Azure AD: User repository used to manage the lifecycle of identities and their entitlements.
- Target system: Application or system that has SCIM endpoint and works with the Azure AD provisioning to enable automatic provisioning of users and groups.
Provisioning using SCIM 2.0
The Azure AD provisioning service uses the SCIM 2.0 protocol for automatic provisioning. The service connects to the SCIM endpoint for the application, and uses SCIM user object schema and REST APIs to automate the provisioning and de-provisioning of users and groups. A SCIM-based provisioning connector is provided for most applications in the Azure AD gallery. When building apps for Azure AD, developers can use the SCIM 2.0 user management API to build a SCIM endpoint that integrates Azure AD for provisioning
App provisioning lets you:
- Automate provisioning: Automatically create new accounts in the right systems for new people when they join your team or organization.
- Automate deprovisioning: Automatically deactivate accounts in the right systems when people leave the team or organization.
- Synchronize data between systems: Ensure that the identities in your apps and systems are kept up to date based on changes in the directory or your human resources system.
- Provision groups: Provision groups to applications that support them.
- Govern access: Monitor and audit who has been provisioned into your applications.
- Seamlessly deploy in brown field scenarios: Match existing identities between systems and allow for easy integration, even when users already exist in the target system.
- Use rich customization: Take advantage of customizable attribute mappings that define what user data should flow from the source system to the target system.
- Get alerts for critical events: The provisioning service provides alerts for critical events and allows for Log Analytics integration where you can define custom alerts to suit your business needs.
HR application to AAD user provisioning

If you want to read more about AWS Identity and Access management, you can get more info here.

I personally think that You should now Microsoft, Amazon and Google services, at least the concepts so You can design viable solutions based to multi-cloud models.
This is just my opinion and based on my personal experiences.
Things to remember
Custom non-gallery apps:
You need the following to add a custom app.
| Identifier (Entity ID) | Uniquely identifies the application. Azure AD sends the identifier to the application as the Audience parameter of the SAML token. The application is expected to validate it. |
| Reply URL | Specifies where the application expects to receive the SAML token. The reply URL is also referred to as the Assertion Consumer Service (ACS) URL |
You can sync your on-premises extension attributes with AAD Connect.
You can add custom claims for the application to retrieve.
Applications will be in myapplication.microsoft.com if You publish them there.
Gallery apps:
You can also add here custom claims for the application to retrieve.
Applications will be in myapplication.microsoft.com if You publish them there.
Provisioning:
User provisioning can be established example with SAML federation.
You can create users from Azure AD to external targets like Google and AWS with SCIM endpoints.
Provisioning can be done manually or automatically.
SCIM:
- Automate provisioning: Automatically create new accounts in the right systems for new people when they join your team or organization.
- Automate deprovisioning: Automatically deactivate accounts in the right systems when people leave the team or organization.
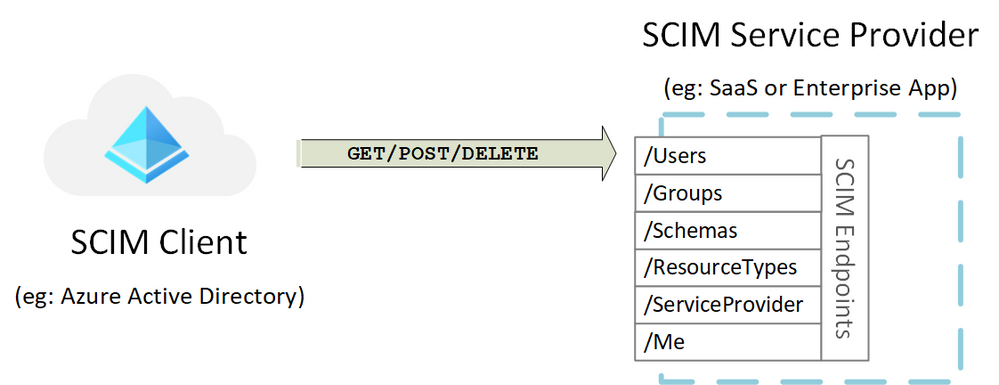
SCIM 2.0 (aka IETF RFC 7643 and RFC 7644) defines a standardized API which a client can call to perform typical representational state transfer (REST) operations on resources such as users and groups. There is even a standardized schema so implementers know what kinds of attributes to use within requests.

 RSS - Posts
RSS - Posts