
In this post I will be covering Azure Application Gateway.
Table of Contents
What is Application gateway?
Azure Application Gateway is a web traffic load balancer that enables you to manage traffic to your web applications. Traditional load balancers operate at the transport layer (OSI layer 4 – TCP and UDP) and route traffic based on source IP address and port, to a destination IP address and port.
Application Gateway can make routing decisions based on additional attributes of an HTTP request, for example URI path or host headers.
Pricing
Application Gateway
| Application Gateway Type | Basic Application Gateway | Web Application Firewall Application Gateway |
|---|---|---|
| Small | €0.0252 per gateway-hour (~€18.334/month) | Not available |
| Medium | €0.0704 per gateway-hour (~€51.334/month) | €0.1266 per gateway-hour (~€92.401/month) |
| Large | €0.3215 per gateway-hour (~€234.669/month) | €0.4501 per gateway-hour (~€328.537/month) |
Data processing
Data processing charge is based on the amount of data processed by the application gateways.
| Data Processing | Price |
|---|---|
| Small | |
| Unlimited | €0.0072 per GB |
| Medium | |
| First 10 TB/month | Included |
| Over 10 TB/month | €0.0063 per GB |
| Large | |
| First 40 TB/month | Included |
| Over 40 TB/month | €0.0032 per GB |
How to create Application Gateway?
Creating the resource
Search for Application inside Azure portal. Once You get it open, You will see it under Load balancing Services. I covered

An application gateway is a web traffic load balancer that enables you to manage traffic to your web application.
For the Tiers: The v2 tiers offer performance enhancements and support for some critical new features. Choose a WAF tier to support Web Application Firewall on this application gateway. You can upgrade to a WAF tier after the application gateway has been created.

For minimum instance count: Additional reserved capacity which is always maintained irrespective of traffic. 0 signifies purely autoscaling Application Gateway with no additional reserved capacity while still maintaining high availability of the service.
And for Availability zone: Some regions support the ability to put your v2 application gateway in an availability zone (or multiple, for zone redundancy). If you’re not able to select a zone, you may have chosen an Azure region that doesn’t yet support availability zones.

Choose a virtual network from the selected subscription and location. You’ll need a virtual network that has an empty subnet, or a subnet that only contains application gateways. You can also create a new virtual network and subnet.
You can select subnets that are empty or that only contain application gateways.

Frontend
Traffic enters the application gateway via its frontend IP address(es). An application gateway can use a public IP address, private IP address, or one of each type.
You can create Public, Private or both address types.

Note! Application Gateways with a tier of Standard_v2 don’t support only private IP addresses as the frontend. Supported SKU tiers are standard and WAF.
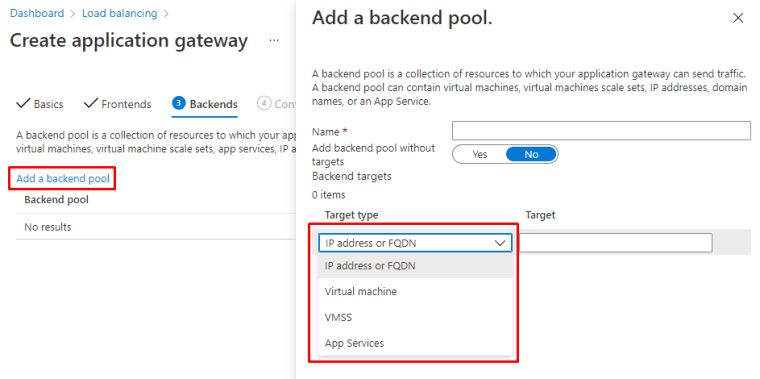
Backend
A backend pool is a collection of resources to which your application gateway can send traffic. A backend pool can contain virtual machines, virtual machine scale sets, app services, IP addresses, or fully qualified domain names (FQDN).
You the following Backend options available. I will choose Virtual machine
Routing rules
Listener
Choose listener specific settings, note that Listener name cannot be changed after this.
In here You can also choose the Frontend ip’s, Public and Private.

Backend targets
Backend pool

Redirection
Inside Redirection You can choose type from Permanent, Temporary or Found.

Completing setup
Now You should be having these displayed.

Adding a VM to backend pool
You can also provision an VM and add it to Application gateway from the start.

And You will App GW in the review screen.

Health probe
You can also add an health probe for the backend endpoints.

Custom health probe settings
The following table provides definitions for the properties of a custom health probe.
| Probe property | Description |
|---|---|
| Name | Name of the probe. This name is used to identify and refer to the probe in back-end HTTP settings. |
| Protocol | Protocol used to send the probe. This has to match with the protocol defined in the back-end HTTP settings it is associated to |
| Host | Host name to send the probe with. In v1 SKU, this value will be used only for the host header of the probe request. In v2 SKU, it will be used both as host header as well as SNI |
| Path | Relative path of the probe. A valid path starts with ‘/’ |
| Port | If defined, this is used as the destination port. Otherwise, it uses the same port as the HTTP settings that it is associated to. This property is only available in the v2 SKU |
| Interval | Probe interval in seconds. This value is the time interval between two consecutive probes |
| Time-out | Probe time-out in seconds. If a valid response isn’t received within this time-out period, the probe is marked as failed |
| Unhealthy threshold | Probe retry count. The back-end server is marked down after the consecutive probe failure count reaches the unhealthy threshold |
Backend health
When the backend pool resources are healthy, You will see the following with status 200

Trying out balancing
When You go to main page, You will see the App GW public address.

And You can see the IIS website Your are balancing.

Deployment with ARM-template
Microsoft has and excellent article for the ARM-templates.

If You want to deploy the test environment with templates, you can use this one.

What it will deploy?
Multiple Azure resources are defined in the template:
- Microsoft.Network/applicationgateways
- Microsoft.Network/publicIPAddresses : one for the application gateway, and two for the virtual machines.
- Microsoft.Network/networkSecurityGroups
- Microsoft.Network/virtualNetworks
- Microsoft.Compute/virtualMachines : two virtual machines
- Microsoft.Network/networkInterfaces : two for the virtual machines
- Microsoft.Compute/virtualMachine/extensions : to configure IIS and the web pages
Diagnostic logs
You can use different types of logs in Azure to manage and troubleshoot application gateways. You can access some of these logs through the portal. All logs can be extracted from Azure Blob storage and viewed in different tools, such as Azure Monitor logs, Excel, and Power BI. You can learn more about the different types of logs from the following list:
- Activity log: You can use Azure activity logs (formerly known as operational logs and audit logs) to view all operations that are submitted to your Azure subscription, and their status. Activity log entries are collected by default, and you can view them in the Azure portal.
- Access log: You can use this log to view Application Gateway access patterns and analyze important information. This includes the caller’s IP, requested URL, response latency, return code, and bytes in and out. An access log is collected every 60 seconds. This log contains one record per instance of Application Gateway. The Application Gateway instance is identified by the instanceId property.
- Performance log: You can use this log to view how Application Gateway instances are performing. This log captures performance information for each instance, including total requests served, throughput in bytes, total requests served, failed request count, and healthy and unhealthy back-end instance count. A performance log is collected every 60 seconds. The Performance log is available only for the v1 SKU. For the v2 SKU, use Metrics for performance data.
- Firewall log: You can use this log to view the requests that are logged through either detection or prevention mode of an application gateway that is configured with the web application firewall. Firewall logs are collected every 60 seconds.
Things to remember
Application Gateway and resources have to be in the same Virtual network, just create new subnets under Virtual network.
Frontend is Application GW public interface, Backend pool contains the resources that will be balanced.
Application Gateway is a Load balancing solution, other similar are.
Front Door: Azure Front Door Service is Microsoft’s highly available and scalable web application acceleration platform and global HTTP(s) load balancer. It provides built-in DDoS protection and application layer security and caching.
Load balancer: With built-in load balancing for cloud services and virtual machines, you can create highly-available and scalable applications in minutes. Azure Load Balancer supports TCP/UDP-based protocols such as HTTP, HTTPS, and SMTP, and protocols used for real-time voice and video messaging applications.
Traffic manager: Azure Traffic Manager is a DNS-based traffic load balancer. This service allows you to distribute traffic to your public facing applications across the global Azure regions. Traffic Manager also provides your public endpoints with high availability and quick responsiveness.
Azure Application Gateway supports integration with Key Vault for server certificates that are attached to HTTPS-enabled listeners. This support is limited to the v2 SKU of Application Gateway.
Application Gateway offers two models for TLS termination:
- Provide TLS/SSL certificates attached to the listener. This model is the traditional way to pass TLS/SSL certificates to Application Gateway for TLS termination.
- Provide a reference to an existing Key Vault certificate or secret when you create a HTTPS-enabled listener.


 RSS - Posts
RSS - Posts